Implementation of a Catadioptric Imaging System for 3D Data Acquisition

A catadioptric stereo system uses scene reflections in a mirror for capturing stereo images with a single camera. Rotationally symmetric mirrors have improved geometric properties compared with planar mirrors. In this diploma thesis, the implementation of a catadioptric imaging system using the inside of a hollow truncated cone as mirror is described. The different necessary steps for the implementation are explained, and an evaluation of the achieved results is given. Additional to the practical implementation also a synthetic setup of the catadioptric imaging system is built, delivering ground truth for error measurements.
Author: Sebastian Knorr
Supervisors: Hendrik Lensch, Michael Weber
Advisers: Holger Dammertz, Johannes Hanika
Context: Diplom thesis (2008)
Conditional Pseudonymity in Vehicular Ad-Hoc Networks
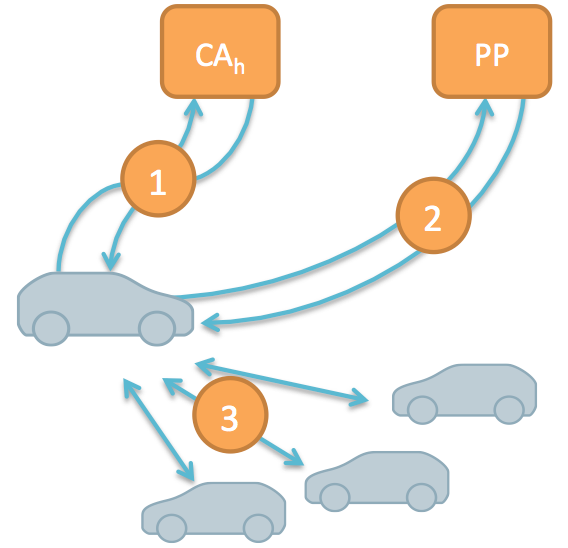
Privacy is an important issue in future vehicle networks, because vehicles broadcast detailed information. Also of importance is accountability due to safety critical applications. Conditional pseudonymity, i.e., the usage of resolvable pseudonyms, is a common approach to address both. Often, resolvability of pseudonyms is achieved by authorities maintaining pseudonym-identity mappings. However, these mappings are privacy sensitive and require strong protection to prevent abuse or involuntary leakage. We developed a new approach that does not rely on pseudonym-identity mappings to be stored by any party. Resolution information is directly embedded in pseudonyms and can only be accessed when multiple authorities cooperate for identity resolution. Our privacy-preserving pseudonym issuance protocol ensures that pseudonyms contain valid resolution information but prevents issuing authorities from creating pseudonym-identity mappings.
| Author: | Florian Schaub |
| Adviser: | Zhendong Ma |
| Supervisors: | Michael Weber, Frank Kargl |
| Context: | Diplom thesis (2008) |
| Resources: | Thesis, PASSAT09 paper, WCNC10 paper |
Fault-tolerant Security Mechanisms for Aggregation in Vehicular Networks
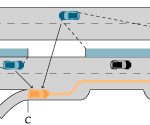
Vehicle-to-vehicle networks enable a multiude of new applications to make driving safer, more efficient, and convenient. The large number of potential applications in combination with the bandwidth restricted wireless communication channel many applications will need to aggregate information and disseminate those aggregates rather than single messages. This communication pattern introduces security issues because the original sender cannot be determined unambiguously anymore. Several security mechanisms were developed in this thesis to secure aggregation protocols.
Author: Stefan Dietzel
Advisers: Elmar Schoch, Boto Bako
Supervisors: Michael Weber, Frank Kargl
Kontext: Diplom thesis (2008)
