Guide to a secure home office
This guideline is intended to reduce uncertainty with regard to work in the home office by showing procedures and assistance which increase the security of processing in private rooms as well.
In any case, it is important that supervisors and employees are equally aware of the risks involved in moving the activity to another workplace that is not under the direct influence of the employer.
This can have a particular effect when special solutions secure the working environment that are not available in the home office. This makes it all the more important to reliably implement the obvious security measures.
In any case, a minimum of security measures must be established, at best on a case-by-case basis.
As a rule of thumb, measures that prevent unauthorised persons from taking note of work content at the university workstation should also be aimed for in the home office.
Requirements for the employees
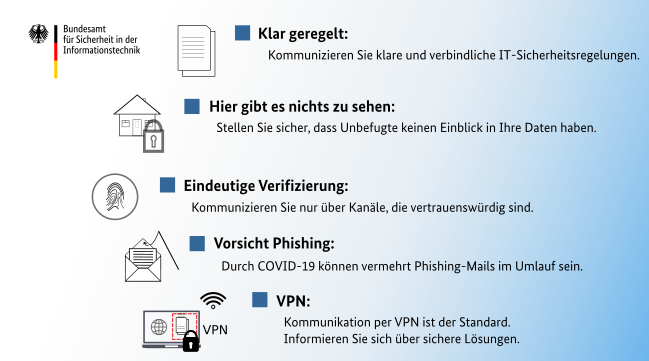
Take care of your surroundings
Clean Desk
A clean, tidy workplace is as simple as it is effective. Make sure that there are no documents, printouts, copies, notes or other data carriers, whether in paper or digital form, lying around at your home office or desk when you leave it. If you implement this consistently, there is no need to decide on a case-by-case basis whether data must be kept confidential. Be consistent, careful and aware of your responsibility as an employee.
Printouts
Avoid printouts whenever possible. This not only helps the environment, but can also be the first step to avoid subsequent problems such as data protection-compliant document destruction and storage.
As soon as you print a document, you release it from the security environment designed at the university. You must be able to personally ensure the handling of the printout and its security.
Phone calls
Pay attention to acoustic privacy. Internal information can not only be seen visually, but also through telephone calls, conversations, etc. without authorization. This also affects information that is worth protecting for other reasons, such as research results.
Carefully choose the right place for business and especially confidential telephone calls. Ensure that conversations cannot be overheard by third parties. Keep the windows closed if an open window could allow third parties to listen in on the call.
Also, avoid making phone calls in public if you cannot ensure that calls may be overheard.
Segregation of spheres of life
Work at home
In the case of workplaces in the home office, care must be taken from the outset to ensure that appropriate safety measures can be created, taking into account structural and spatial conditions (e.g. separate work or office area).
For the domestic workplace, the use of a separate study is desirable, if your living conditions allow it. At the very least, the home office should be separated from the rest of the home by a lockable door so that documents and IT systems located there are outside the areas where other people are present. In the event of spontaneous visits, the workplace can thus be left at short notice and protected against unauthorised access and entry.
IT usage
If possible, use the IT equipment (hardware and software) provided by the university for work in your home office. In particular, do not use private devices (PC, notebook, smartphone, USB stick, etc.) for processing personal data, unless this has been explicitly permitted by the university.
If you establish a VPN connection from your private device to the university network and connect to your work computer at the university using RDP (or a comparable remote desktop protocol), data processing takes place within the university's protected IT environment. This access is therefore preferable if the university does not or cannot provide you with a business terminal for working in your home office.
Any other use of private IT end devices can infect the company's IT infrastructure with malware and entail considerable risks.
Organization
Organize yourself and your work in such a way that you can carry out your activities without the help of private IT and private programs.
Under no circumstances is the forwarding of official, confidential communication to a private mail account permitted.
Security measures
Internet access
Protect your private Internet access. Especially the private area is especially attractive for social engineering. In addition, attacks can be carried out more easily via private or public networks.
You should therefore ensure that your network prevents unauthorized use. Choose a secure password (s. Password policy of the University Ulm).
Access to the workplace
Prevent unauthorized third parties from gaining access to your workstation or to content you are processing. Align your screen so that it cannot be seen by pedestrians on the street (from outside), for example.
Do not leave your PC unattended even in your home office, unless no other person has potential access to it. For example, lock the screen if you leave your workplace for a short time, just as you should do at your university workplace. This helps to protect the integrity of the data.
Last but not least, you should ask whether it is necessary to lock the study, a desk drawer or a filing cabinet. In particular, if printouts are absolutely necessary for you to be able to carry out your work, you must consider locking options.
Requirements for superiors
Creating and shaping free space
Conception - Who, how, what, when?
Act proactively and conceptualize who is allowed to use home office, how often or at what times this is allowed. The basis for the decision on whether or not to use a home office as well as the design of a home office are laid down in the University's teleworking service agreement.
In this way, the right approach can be implemented in a structured manner and the right conditions created. It is also clear to the employees from the outset whether home office is an option for them and under what conditions this is possible.
Infrastructure
IT equipment
If you are planning home office solutions, you can create the right basis for your employees with the appropriate IT equipment. In order to ensure a smooth transition between presence and home office, the use of secure mobile devices is crucial. The changeover can also be made easier by dialing into university systems via VPN.
IT-Configuration
Protect the use of mobile devices against the additional risks associated with mobility.
The following measures help to establish secure systems:
- standard encryption of hard disks (for Windows: BitLocker)
- Access to the operating system only possible via access data with user name and password (as well as biometric features if necessary)
- Automatic blocking of the system already after a short period of inactivity
- Allow access to sensitive systems only via secure connections
- Allow connection to the Internet only via VPN on the system side
Useful equipment
Think through the process of processing information and personal data from start to finish. Provide solutions for each stage of data processing.
Particular attention shall be paid to the destruction of any printouts or notes. Few employees have a document shredder at home that meets the DIN requirements in order to manage the destruction of paper data carriers according to your needs. If shredders or data bins cannot be provided, an arrangement can be made to oblige employees to destroy such documents at work.
Recognize and avoid workarounds
Always pay attention to whether so-called workarounds are emerging at the university. Workarounds occur when the given working method is cumbersome and not suitable for practical use. Proceed with a sense of proportion and do not forget to convince your employees of the implementation. Only practiced security measures can ensure adequate protection.
![[Translate to english:] Homeoffice](/fileadmin/website_uni_ulm/kiz/it/informationssicherheit/Homeoffice_Apple.png)
Communication and Information Centre (kiz)
Please contact us if you have questions or problems related to the kiz services:
Office hours
Monday - Thursday
09:00 h - 12:00 h and 13:00 h - 15:30 h
Friday 09:00 h - 12:00 h
Phone
+49 (0) 731 / 50 - 30000
Telefax
+49 (0) 731 / 50 - 1230000
Order a Callback
helpdesk(at)uni-ulm.de
Support Portal (Uni internal)
[more]
Service Points are locations where you can visit us personally.
Using self-service functions of the Identity Management System (IDM): Administer permissions, subscribe to services, change passwords.
Research in the library stock: monographs, textbooks, magazines, university publications, e-books, e-journals, national licenses, and the contents of the institutional repository OPARU.
With about 400 keywords you will get direct access to our services. If something isn't listed, please contact our Internet Editorial Office.